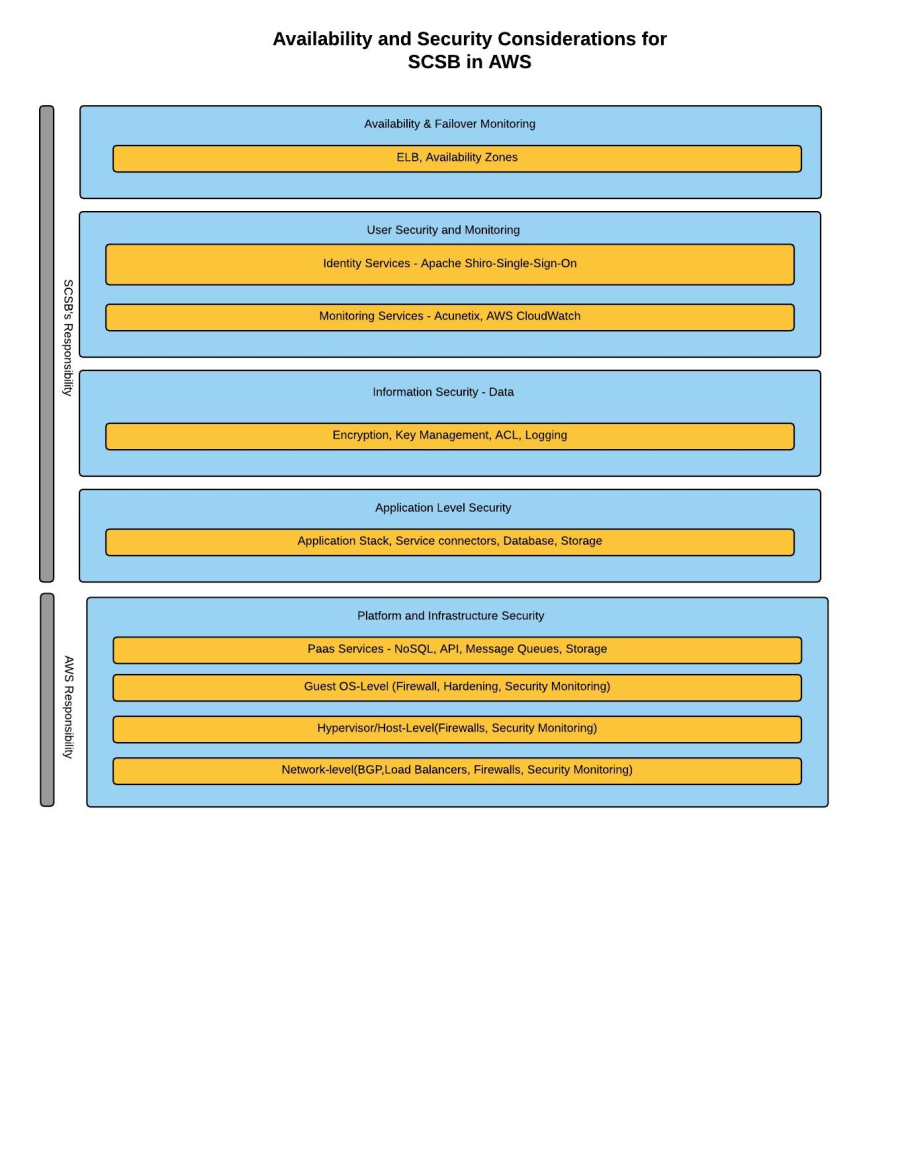
The AWS infrastruture and application architecture takes into consideration various aspects of Software as a Service (SaaS) model of which Security is paramount. The following considerations have been taken into account and implemented.
Image Reference (View larger image):https://www.lucidchart.com/documents/view/e69eb1aa-aeb2-46b2-800a-e1b72ad7d61d+
- Availability and Failover Monitoring
- Availability:
- Minimum: 99%
- Target: 99.9%
- Exceptions:
- Planned upgrades, maintenance.
- AWS outages, although SCSB will have failover strategies to minimize the downtime.
- Reporting:
- Metrics on uptime, any upgrades etc will be made available.
- Availability:
- Backups:
- Nightly
- Amazon Machine Images (AMIs)
- Failover:
- N+1 redundancy setup
- AWS Elastic Load Balancer (ELB).
- Multiple AZs (Availability zones) to increase fault tolerance.
- Monitoring:
- Amazon Cloud Watch
- DDOS Risk mitigation:
- Whitelisting IPs
- Blacklisting IPs
- User Security and Monitoring
- User Data: SCSB doesn't store any confidential/private or sensitive information about the users.
- Identity Services:
- Authentication via SSO/Apache Shiro
- Authorization via local roles/permissions in SCSB
- Vulnerability Scanning:
- Acunetix: Security vulnerability scanner.
- SSH Security Groups:
- Secure access for support personnel to do maintenance/upgrades/support
- Information Security - Data:
- SCSB does not store any patron sensitive information.
- SCSB stores library collection information (Bibliographic, Holdings, Items) which are public records and not deemed sensitive.
- Audit trail information available showcasing who has accessed/modified data restricted by permissions.
- Application Level Security :
- Data encryption to be enforced by partners while invoking SCSB REST services.
- SCSB will deploy SSL certificate for data encryption for SCSB UI.
- JSON webtoken for RESTful services
- Monitoring Services: Acunetix: Application security vulnerability scanner.
- Platform and Infrastructure Security :
- Amazon is responsible for this part as the cloud hosting provider.